- Armitage : Graphical Cyber Attack Management Tool

Armitage
is a graphical cyber attack management tool for Metasploit that
visualizes your targets, recommends exploits, and exposes
the advanced capabilities of the framework. Armitage
aims to make Metasploit usable for security practitioners who
understand
hacking but don’t use Metasploit every day. If you want to learn Metasploit and grow
into the advanced features, Armitage can help yo
---------------------------------------------------------
2.Dark-Jumper v5.8 : SQLi, LFi RFi Scanner
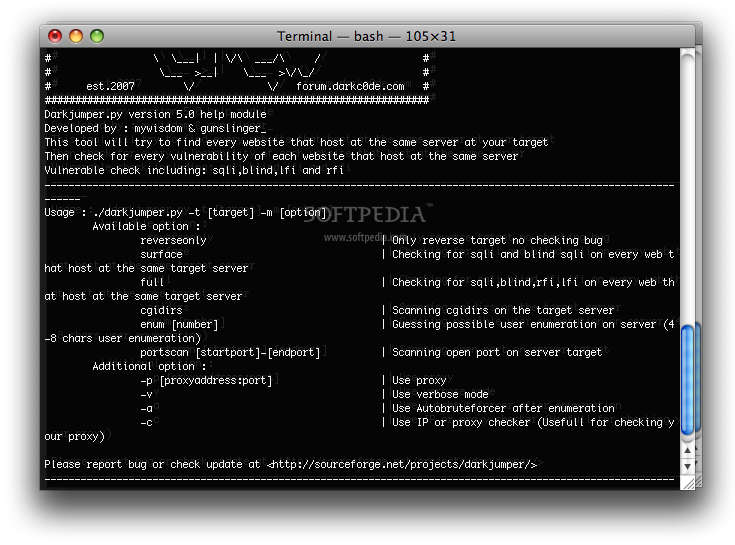
Darkjumper
is a free tool what will try to find every website that hosts at the
same server as your target. Then check for every vulnerability of
each website that host at the same time
Download Link http://mac.softpedia.com/get/Security/Darkjumper.shtml
---------------------------------------------------------
3.Dossier detective (information gathering/doxing tool coded by me)
Dossier Detective:
![[Image: dossier%20detective%20screenie.jpg]](http://dreamwalk.yolasite.com/resources/dossier%20detective%20screenie.jpg)
This tool takes advantage of the freely available public information on the internet in an attempt to create a dossier on individuals and companies by using a plethora of techniques. It will do things like use search engines, social networking sites, vehicle databases, telephone systems and much more. Primarily
aimed at private detectives but obviously not restricted to - coded in VC++ and required the .NET
rumtime 3.5 or above to run.
ONLY ONLY FOR EDUCATIONAL PURPOSE
---------------------------------------------------------
4.Lucidity Scanner (check vulnerable computers, webservers, DoS attack etc)
coded by me
coded by me
This is the BEST tool I've made to date:
![[Image: lucidty%20screenshot.jpg]](http://dreamwalk.yolasite.com/resources/lucidty%20screenshot.jpg)
Lucidity Scanner
This is a tool for checking and testing computers and web servers which can help build up a blueprint of the system and identify potentially exploitable weaknesses.
---------------------------------------------------------
5.iPentagram - ShellBooter, DorkScanner, Vuln.Scanner, IPTracer, TxtEncrypt [MediaFire]
![[Image: jbpZAXH5JiQlqu.png]](http://i.minus.com/jbpZAXH5JiQlqu.png)
What is iPentagram?
iPentagram is a project I have been working on for the past few weeks.It includes a large variety
of functions which are mandatory for all computer lovers and enthusiasts.
Features:iPentagram is a project I have been working on for the past few weeks.It includes a large variety
of functions which are mandatory for all computer lovers and enthusiasts.
- // Shell Booter - Powerful and advanced shellbooter which gives the users the ability to add new shells.
- // Dork Scanner - Scan websites for dorks with blazing speeds.
- // Vulnerability Detector - SQLi vulnerability detector with multiple settings.
- // IP Tracer - Trace, log and export IP addresses.
- // File Pumper - Increase the size of your executables without corrupting it.
- // Text Encryption/Decryption -
- Gives the user the ability to encrypt or decrypt submitted text.
- // Multi-threaded - iPentagram is fully multi-threaded. Meaning, you can run multiple tools at once without causing the application to freeze or crash.
- // User Friendly - iPentagram was designed to be used not only by professionals but also by beginners and is therefore extremely user friendly. With messages and tooltips that even a child could understand, iPentagram is as easy as it gets.
- // Automatic Updates - iPentagram will automatically notify the user when a new update is available and will allow the user to get his/her hands on the new update with just the click of a button.
NOTE:
Do not remove/relocate the files associated with iPentagram or it may not work.
Do not remove/relocate the files associated with iPentagram or it may not work.
6.Flutter Packets [DOS]
![[Image: zWfu8TO.png]](http://i.imgur.com/zWfu8TO.png)
![[Image: 2vi1747.png]](http://i40.tinypic.com/2vi1747.png)
Also the ftp brute was disabled in public version
For penetration testing only
Download Link
![[Image: zWfu8TO.png]](http://i.imgur.com/zWfu8TO.png)
Download Binray here
Download Source here
---------------------------------------------------------
7.CPanel Nightmare - puplic Version
![[Image: 2vi1747.png]](http://i40.tinypic.com/2vi1747.png)
This is the public version
This version is 3 times slower from private versionAlso the ftp brute was disabled in public version
For penetration testing only
Download Link
Login Password: pentest
---------------------------------------------------------
8. 2.BlaZer's Tool Kit - All in One Hacking Tools Pack : Free Download

Features:
★ Inbuilt Web Browser with Java Script and Flash
★ Email Bomber
★ Port Scanner
★ Screen Recorder
★ Pinger
★ Anti-Virus Finder
★ File-Downloader and much more.....
Download Now
http://www.mediafire.com/?9qa37of7ihd1z
http://www.mediafire.com/?9qa37of7ihd1z
---------------------------------------------------------
9.Aph3x Stresser V2! Just Him Em Up!
![[Image: 2ylsr4p.jpg]](http://oi47.tinypic.com/2ylsr4p.jpg)
Changes
Fixed some bugs.
Made it more stable.
Works faster.
Should work with any ddos shell out there with no problems.
Added unlimited attack time ( 99999999999?
yea,even more)
Download Link: here
---------------------------------------------------------
10.SQL Injection TOOLs All IN One Complete Pack
| SQL Injection TOOLs All IN One ->Black Out v1.0 ->ExploitSQL_v2_0 ->Google_URLs_Extractor ->Havij1.08 ->Havij1.13 Pro edition ->Hybrid_V02_ ->Hybrid_v.1.0 ->jsky ->Lib ->Longcat ->obeseusvB ->Palector v1 ->pangolin ->QuadNX_v.Qx2 ->Sabre Flood ->SQL_Injection_Tool_v1 ->SQLIHelper_V2.5 ->SQLSmarthack ->tequiLAN_0.1_5 ->WITOOL_V0.1_081231 ->xdos |
---------------------------------------------------------
11.On Cracking Rampage OCR 1.14 Tool
![[Image: tvocr.jpg]](http://i1114.photobucket.com/albums/k539/wizevil/tvocr.jpg)
Download
Cracking Rampage OCR
---------------------------------------------------------
12.Here is a decent little cracker. It requires a proxy list but gets good results. Enjoy
![[Image: y1XiOTx.png]](http://i.imgur.com/y1XiOTx.png)
---------------------------------------------------------
13.SMTP SCANNER
![[Image: 45995_257x193.jpg]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhf4l3kqsp7pKy-mGzNLX73yf0G1Sh3DCI3ve1zkoqGNw_U4b5mN8-5cNfxe8GKj9VMhTQUbd3kXp2cddtWL4MFmt5O51WBbt5WgjqSJBFbNDl62CZPKK-VvOE1dp4Jl5BemGxoenFSA7U/s1600/45995_257x193.jpg)
The powerful tool to your email marketing service. Use SMTP SCANER, you can find out
many workable SMTP servers in few hours or days. It is can check the SMTP server
(Relay SMTP Server and Anonymous SMTP Server). It can use hundreds of threads/connections
to search
Click here To download
---------------------------------------------------------
14. Exploit Scanner
Here a Exploit Scanner very easy to use.
Have fun and hack as many you could :dance:
Click here to download
---------------------------------------------------------
15.WordPress Site Bruce Force
![[Image: 1ifXL]](http://puu.sh/1ifXL)
Click here to download
---------------------------------------------------------
16.Ez File Pumper
A pumper makes a file bigger. (the size of the file) So if you have a virus, and its 2kb, nobody will download it because its definitely not anything real, so if you make the
file to say 2mb people wont think twice about it. So lets just say you made a virus,
but the size is way to small and people will not download it because of the size.
So what do you need... The Ez File Pumper!!!!
![[Image: 2jfkr5k.jpg]](http://i44.tinypic.com/2jfkr5k.jpg)
Click Here To DOwnload
---------------------------------------------------------
17.Source DecFlooder v1.00
Features:
Flooder:
DDos
Email Bomber
Chat Spammer
![[Image: 45995_257x193.jpg]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhf4l3kqsp7pKy-mGzNLX73yf0G1Sh3DCI3ve1zkoqGNw_U4b5mN8-5cNfxe8GKj9VMhTQUbd3kXp2cddtWL4MFmt5O51WBbt5WgjqSJBFbNDl62CZPKK-VvOE1dp4Jl5BemGxoenFSA7U/s1600/45995_257x193.jpg)
The powerful tool to your email marketing service. Use SMTP SCANER, you can find out
many workable SMTP servers in few hours or days. It is can check the SMTP server
(Relay SMTP Server and Anonymous SMTP Server). It can use hundreds of threads/connections
to search
Click here To download
---------------------------------------------------------
14. Exploit Scanner
Here a Exploit Scanner very easy to use.
Have fun and hack as many you could :dance:
Click here to download
---------------------------------------------------------
15.WordPress Site Bruce Force
Click here to download
---------------------------------------------------------
16.Ez File Pumper
A pumper makes a file bigger. (the size of the file) So if you have a virus, and its 2kb, nobody will download it because its definitely not anything real, so if you make the
file to say 2mb people wont think twice about it. So lets just say you made a virus,
but the size is way to small and people will not download it because of the size.
So what do you need... The Ez File Pumper!!!!
![[Image: 2jfkr5k.jpg]](http://i44.tinypic.com/2jfkr5k.jpg)
Click Here To DOwnload
---------------------------------------------------------
17.Source DecFlooder v1.00
Features:
Flooder:
DDos
Email Bomber
Chat Spammer
18.BLACK HOLE EXPLOIT KIT
![[Image: image_1.jpg]](http://4.bp.blogspot.com/_bCYQxIvMQ2U/Tdn23mOZamI/AAAAAAAACAY/N5u_KmhcMf8/image_1.jpg)
BlackHoleexploit kit is A type of crimeware Web application developed in Russia to
help hackers take advantage of unpatched exploits in order to hack computers via
malicious scripts planted on compromised websites.
help hackers take advantage of unpatched exploits in order to hack computers via
malicious scripts planted on compromised websites.
19.GetSploits - search exploit-db.com database by command line
getsploits searches for specific exploits/shellcode/papers (using several search
options to narrow down the results) from exploit-db.com and prints descriptions
and links to found exploits/shellcode/papers and optionally writes links and
descriptions of found results to a file.
options to narrow down the results) from exploit-db.com and prints descriptions
and links to found exploits/shellcode/papers and optionally writes links and
descriptions of found results to a file.
20.Nmap - The most advanced scanner
If you haven't tried nmap yet, you really should cause it's imho the best
You can get it off http://insecure.org/ , and of course it both works on
windows and linux, thus you can get the source of it too if you want to.
21.Backtrack
The Most Commonly used Tool For hacking recomended by hackers give it a try
22. Kali Linux

Kali is a complete re-build of BackTrack Linux, adhering completely to Debian development
standards. All-new infrastructure has been put in place,
all tools were reviewed and packaged, and we use Git for our VCS.
More than 300 penetration testing tools: After reviewing every tool that was included in BackTrack, we eliminated a great number of tools that either did not work or had other
tools available that provided similar functionality.
More than 300 penetration testing tools: After reviewing every tool that was included in BackTrack, we eliminated a great number of tools that either did not work or had other
tools available that provided similar functionality.
23.Netsparker PentestTool
![[Image: 1.png]](http://www.mavitunasecurity.com/s/ns/ss/full/1.png)
![[Image: 1.png]](http://www.mavitunasecurity.com/s/ns/ss/full/1.png)
This is a tool for Web Penetratition more friendly "Vurnerable
Scanner"
Friendly interface that makes you comfort to use
Scanner"
Friendly interface that makes you comfort to use
Net sparker Community Version [free version]
24. Horny Monkey Deface Builder v1
Horny Monkey Deface Builder is for create your defacement in HTML.
Horny Monkey Deface Builder is for create your defacement in HTML.
Edited! Image links http://prntscr.com/x7pi4
25. AIRCRACK
Aircrack-ng is an 802.11 WEP and WPA-PSK keys cracking program that can recover keys once enough data packets have been captured. It implements the standard FMS attack along with some optimizations like KoreK attacks
26. BarsWF
BarsWF is the worlds fastest md5 bruteforcing password cracker,
just in case you didn't already know It combines using your
computers processor with you graphics cards GPU for computing
the largest amount of hashes as quickly as possible.
Click here to download
---------------------------------------------------------
just in case you didn't already know It combines using your
computers processor with you graphics cards GPU for computing
the largest amount of hashes as quickly as possible.
Click here to download
---------------------------------------------------------
27.BLOODSHED IDE
Bloodshed IDE is an Integrated Development Environment
(IDE) for the C/C++ programming language.
Download Now
---------------------------------------------------------
28. NEMESIS
Nemesis is a packet injector utility that is command line based and supports linux and windows
Download Now
---------------------------------------------------------
29. HPING
Hping is a command-line TCP/IP assembler that supports TCP, ICMP, UDP and RAW-IP protocols also works on Unix systems, Windows, Sun and MacOS's.
download link
---------------------------------------------------------
30. Metasploit:A hackers Real Friend
![[Image: lemjh.png]](http://securemachine.files.wordpress.com/2011/03/lemjh.png)
Metasploit Framework, a tool for developing and executing
exploit code against a remote target machine. Other important
sub-projects include the Opcode Database, shellcode archive,
and security research.
The Metasploit Project is also well known for anti-forensic and
evasions tools, some of which are built into the Metasploit
Framework.
DOWNload Now
---------------------------------------------------------
31. LOIC/Hoic DDOS ATTACK TOOLs
These are very strong ddos attack tools
Download LOIC
DOWNLOAD HOIC
HOPE U LIKE MY TOols Comments will be appreciated :) :)
and like us on facebook
Download Now
---------------------------------------------------------
Nemesis is a packet injector utility that is command line based and supports linux and windows
Download Now
---------------------------------------------------------
29. HPING
Hping is a command-line TCP/IP assembler that supports TCP, ICMP, UDP and RAW-IP protocols also works on Unix systems, Windows, Sun and MacOS's.
download link
---------------------------------------------------------
![[Image: lemjh.png]](http://securemachine.files.wordpress.com/2011/03/lemjh.png)
Metasploit Framework, a tool for developing and executing
exploit code against a remote target machine. Other important
sub-projects include the Opcode Database, shellcode archive,
and security research.
The Metasploit Project is also well known for anti-forensic and
evasions tools, some of which are built into the Metasploit
Framework.
DOWNload Now
---------------------------------------------------------
31. LOIC/Hoic DDOS ATTACK TOOLs
These are very strong ddos attack tools
Download LOIC
DOWNLOAD HOIC
IF U HAVE ANY GOOD TOOL TO SHARE THEN COMMENT I'LL add it too---------------------------------------------------------
HOPE U LIKE MY TOols Comments will be appreciated :) :)
and like us on facebook
---------------------------------------------------------

No comments:
Post a Comment